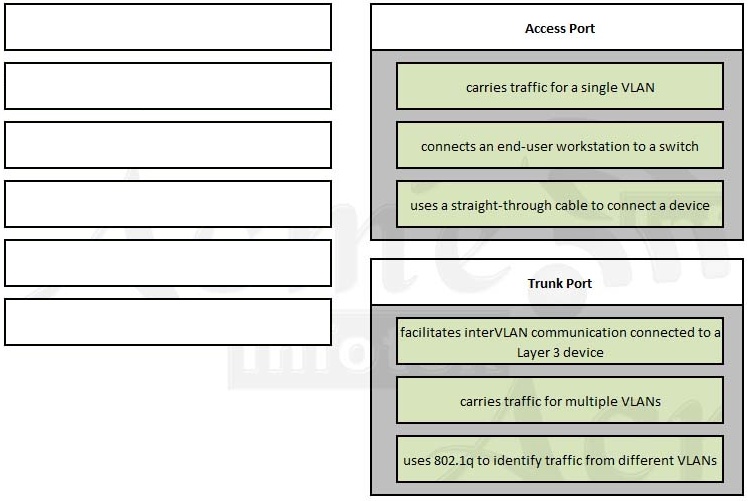
Central Florida Widgets recently installed a new router in their Apopka office. Complete the network installation by performing the initial router configurations and configuring RIPv2 routing using the router command line interface (CLI) on the Apopka router. 
Configure the router per the following requirements:
- Name of the router is Gotha
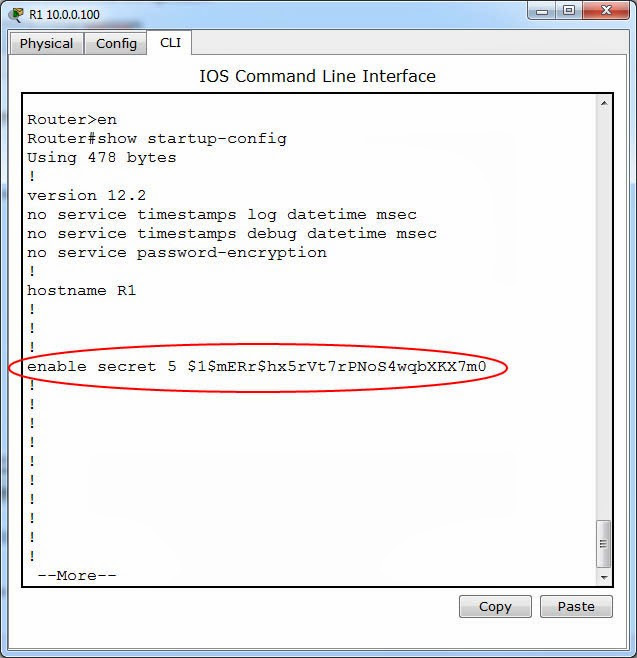
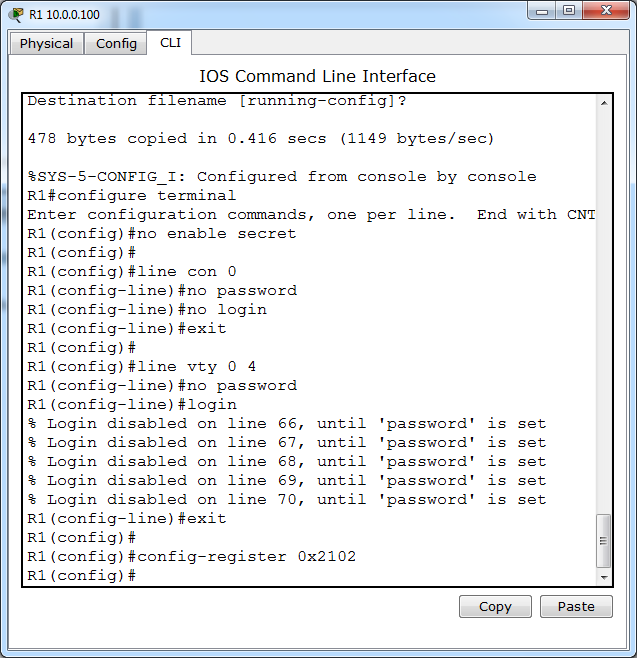
- Enable-secret password is cisco
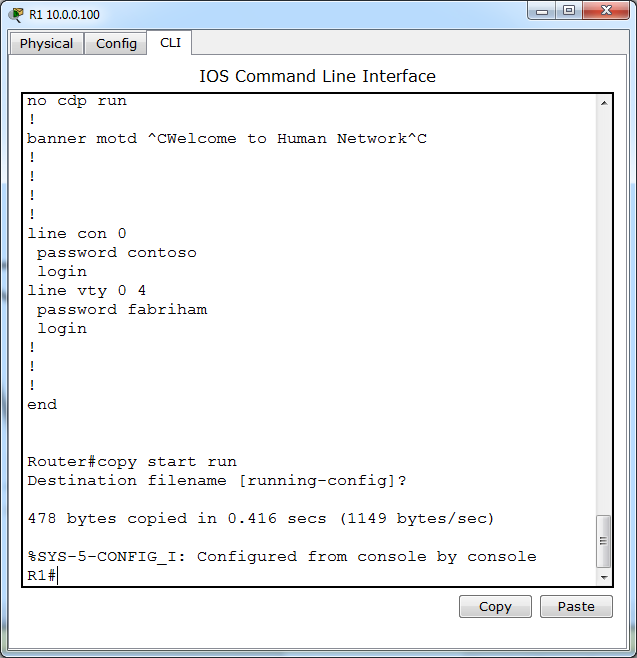
- The password to access user EXEC mode using the console is class
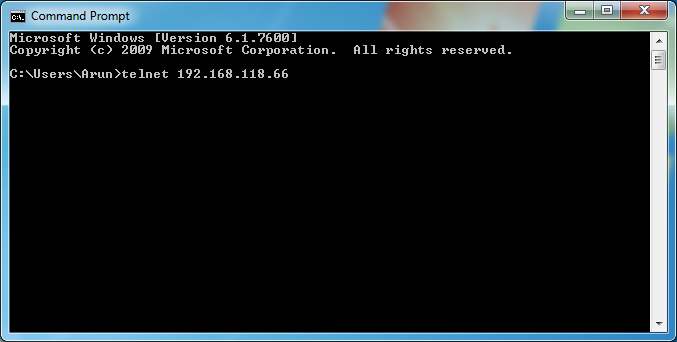
- The password to allow telnet access to the router is class
- IPv4 addresses must be configured as follows:
- Ethernet network 209.165.201.0/27 – router has second assignable host address in subnet.
- Serial network is 192.0.2.128/28 – router has last assignable host address in the subnet.
- Interfaces should be enabled.
- Routing protocol is RIPv2.
Instruction:
To configure the router (Gotha) click on the console host icon that is connected to a router by a serial console cable (shown in the diagram as a dashed black line).
Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar.
The “Tab” key and most commands that use the “Control” or “Escape” keys are not supported and are not necessary to complete this simulation. The help command does not display all commands of the help system.
Explanation:
Step1:
Click on the console host.
Router>
Configure the new router as per the requirements provided in Lab question
Requirement 1:
Name of the router is Gotha
Router>en
Router# conf t
Router(config)# hostname Gotha
Gotha(config)#
Requirement 2:
Enable-secret password is cisco
Gotha(config)# enable secret cisco
Requirement 3:
The password to access user EXEC mode using the console is class
Gotha(config)# line con 0
Gotha(config-line)# password class
Gotha(config-line)# login
Gotha(config-line)# exit
Gotha(config)#
Requirement 4:
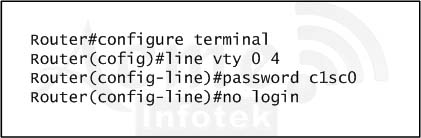
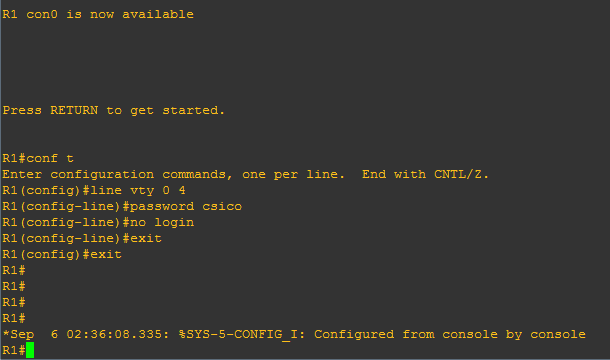
The password to allow telnet access to the router is class
Gotha(config)# line vty 0 4
Gotha(config-line)# password class
Gotha(config-line)# login
Gotha(config-line)# exit
Gotha(config)#
Requirement 5:
a. Ethernet network 209.165.202.128 /27 – Router has the last assignable host address in subnet.
This IP address (209.165.201.158) which we need to configure on Fast Ethernet0/0 of the router using the subnet mask 255.255.255.224
Gotha(config)# interface fa0/0
Gotha(config-if)# ip address 209.165.201.158 255.255.255.224
Gotha(config-if)#no shutdown
Gotha(config-if)#exit
b. Serial Network is 192.0.2.16 /28 - Router has the last assignable host address in subnet.
Serial Network is 192.0.2.16 /28 - Router has the last assignable host address in subnet. We
need to configure Last assignable host address(192.0.2.30) on serial 0/0/0 using the subnet mask 255.255.255.240
Gotha(config)#interface serial 0/0/0
Gotha(config-if)#ip address 192.0.2.30 255.255.255.240
Gotha(config-if)#no shutdown
Gotha(config-if)#exit
Requirement 6:
Router protocol is RIPv2
Need to enable RIPv2 on router and advertise its directly connected networks
Gotha(config)#router rip
Gotha(config-router)# version 2
Gotha(config-router)# no auto-summary
Gotha(config-router)#network 192.0.2.16
Gotha(config-router)#network 209.165.202.128
Gotha(config-router)#end
Step 7:
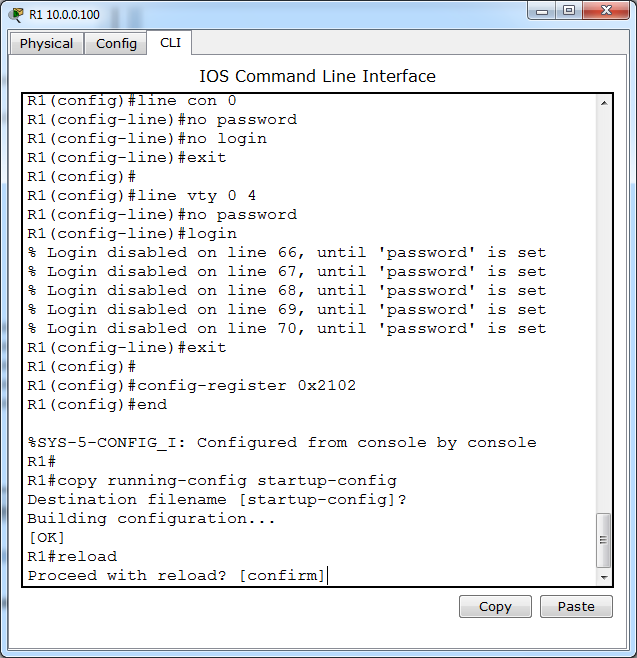
Important please do not forget to save your running-config to startup-config
Gotha# copy run start